Managing AWS IAM Policies in Services Module
Facets provides a declarative approach to managing AWS IAM policies. This document describes the process of managing IAM roles and attaching policies in Facets, with a focus on leveraging dynamic policies for both managed and unmanaged resources.
In the Facets modules pack, IAM roles are automatically created for services, such as Kubernetes deployments, jobs, and cronjobs, based on the module's flavors. Policies can then be attached to these roles to define the required permissions.
Step-by-Step Guide for Attaching Policies to IAM Roles
There are two primary methods for attaching policies to IAM roles in Facets. The following steps outline how to use these methods with the corresponding UI screenshots.
1. Attaching Policies Generated by Managed Resources
Facets ensures that all resources are declarative, meaning resource names and attributes are created only during provisioning. As part of this process, resources output the policies they generate. For example:
- S3 Resources: Generate
READ_ONLYandREAD_WRITEpolicies.
Steps to Attach Generated Policies:
- Navigate to the Cloud Permissions section in the service form.
- Toggle the "Enable IRSA" option if needed to grant fine-grained AWS permissions.
- Under the IAM Policies dropdown, select from the list of policies generated by resources within the project. This dropdown dynamically updates to show all available policies.
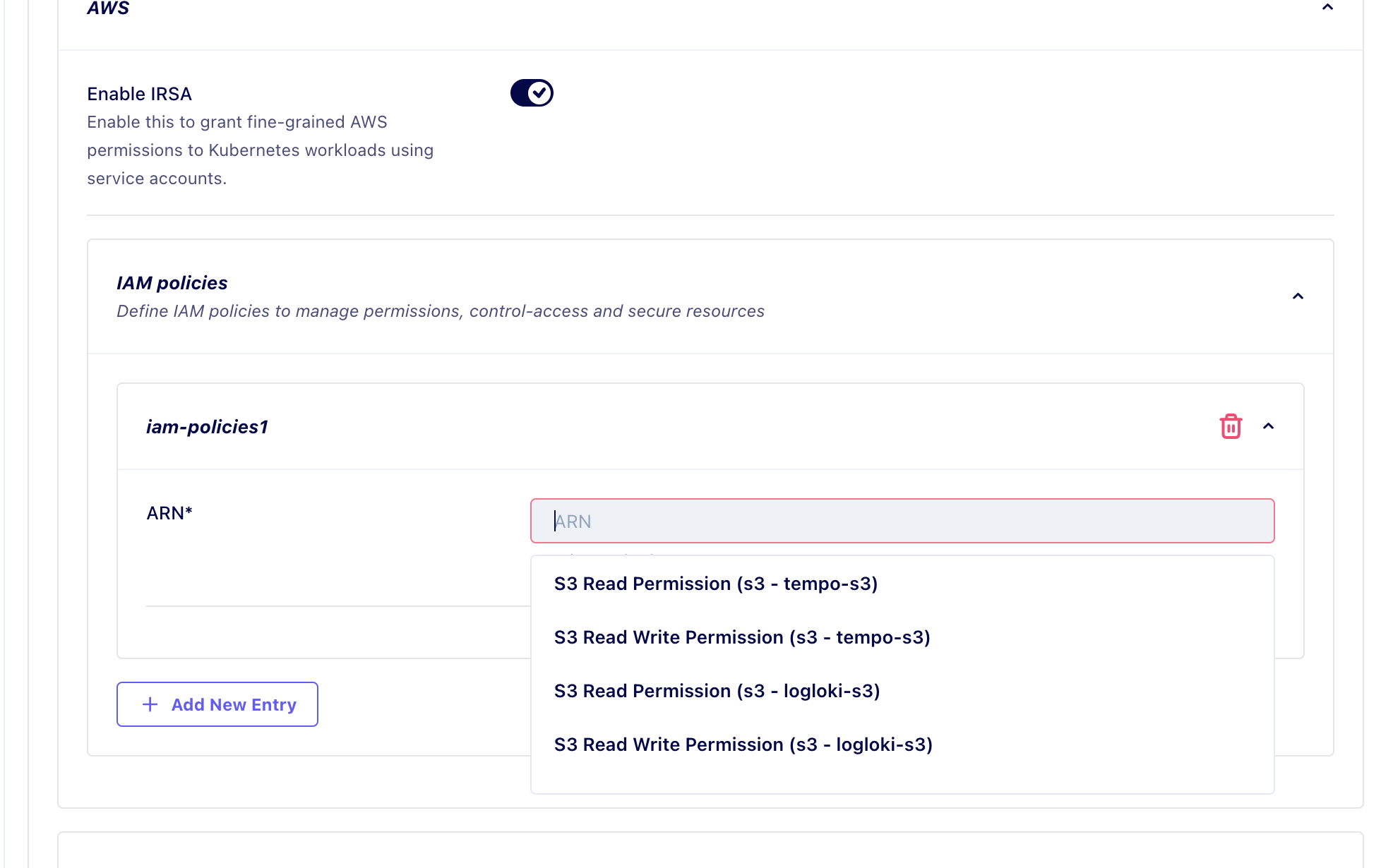
- Select the required policy, such as
S3_READ_ONLYorS3_READ_WRITE, and attach it to the service's IAM role.
This approach removes the need to create policies separately for each environment. This declarative method ensures that policies are consistent and automatically applied even when new environments are provisioned.
2. Attaching Policies for Unmanaged Resources
In cases where a policy is required for resources not managed by Facets, you can create a custom IAM policy directly in the blueprint. These policies can then be referenced in the service form similarly to managed resource policies.
Steps to Create and Attach a Custom Policy:
- Go to the Blueprint Editor and search for "IAM Policy" under resources.
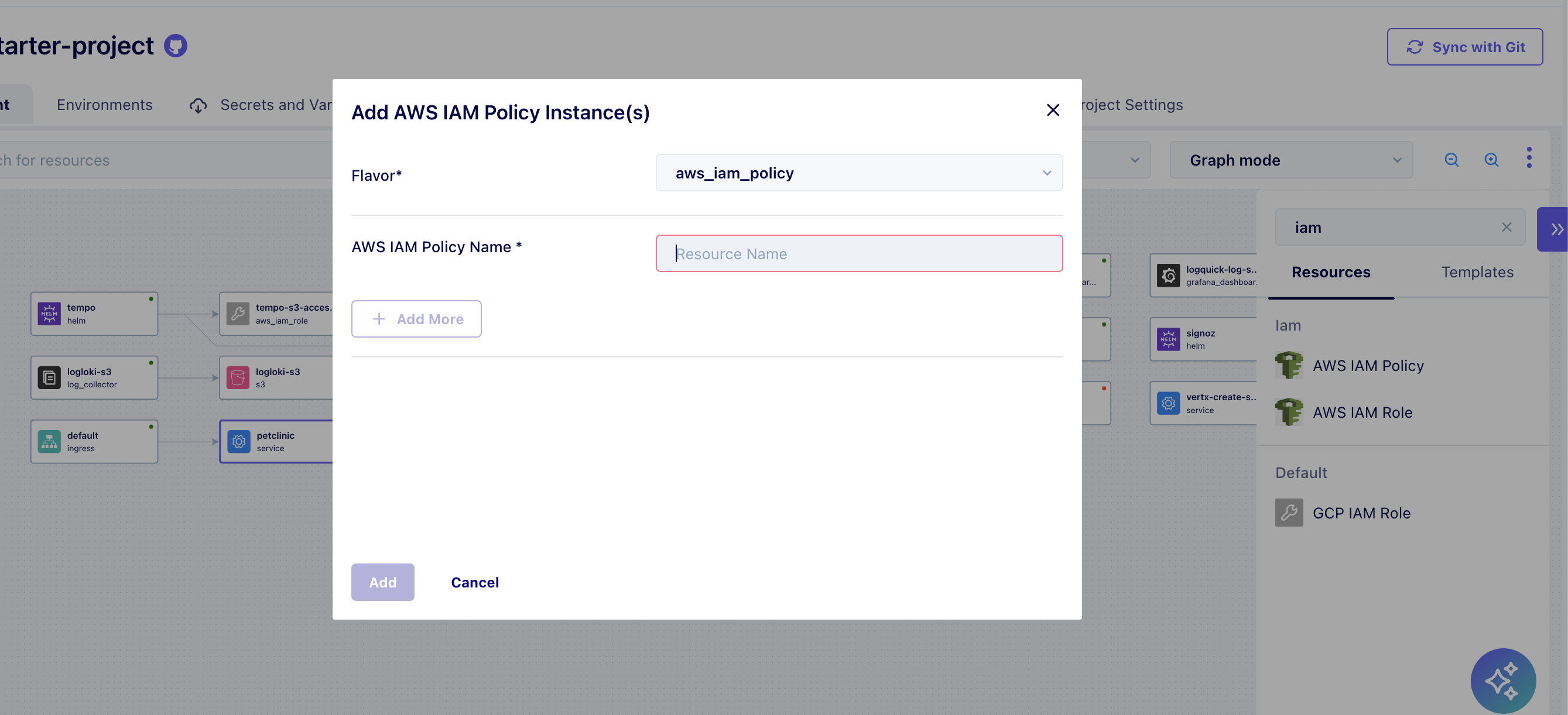
- Add a new IAM Policy resource by selecting the
aws_iam_policyflavor. - Define the policy name and JSON structure in the resource configuration to specify the required permissions.
- Navigate back to the Cloud Permissions section in the service form.
- Under the IAM Policies dropdown, select the custom policy you created. This dropdown dynamically includes all defined IAM policies in the project.
By using this method, you can integrate permissions for external or unmanaged resources declaratively within Facets.
Managing IAM Roles and Policies Across Environments
Facets ensures that IAM policies are applied consistently across all environments. Policies defined once are automatically applied to new environments without requiring additional configuration. This declarative approach simplifies the management of IAM roles and policies across projects and environments.
Key Features of IAM Management in Facets
-
Declarative Management:
- Ensures consistency by defining roles and policies in a declarative format.
- Simplifies updates and changes through version-controlled blueprints.
- Policies are automatically applied across all environments, including new ones.
-
Dynamic Policy Integration:
- Incorporates policies generated by managed resources.
- Supports integration of custom policies for unmanaged resources.
-
Centralized Management:
- Provides centralized control of IAM roles and policies across all services in a project.
Facets standardizes the management of AWS IAM roles and policies, enabling consistent and efficient permission handling. Use the steps and tools outlined above to manage permissions within your projects.
Updated 9 months ago